Having an unsecured subdomain can lead to a serious risk to your business, and lately, there have been some security incidents where the hacker used subdomains tricks. The most recent one was Vine, where the entire code was available to download from a vulnerably exposed subdomain. If you are a website owner or security researcher, you can use the following tools to find the subdomains of any domain.
Subdomains Lookup Tools
Subdomains Lookup tools by WhoisXML API allow users to discover a domain name’s subdomains easily. The subdomains product line is fueled by a comprehensive repository that includes 2.3+ billion subdomain records with 1+ million subdomains added daily. The tools allow researching any target domain name and reveal the list of all subdomains found for the domain with timestamps of the first time the record was seen and the last update for a specific record. The product line includes a/an:
API with output queries in XML and JSON formats for easy integration Data feed with files available in unified and consistent CSV format, updated both on a daily and weekly basis. Download the CSV sample to test the data in your environment GUI lookup tool that creates reports with shareable links
Check this product sheet to learn how WhoisXML API’s subdomain data can match specific data requirements.
DNS Dumpster
DNSDumpster is a domain research tool to find host-related information. It’s the HackerTarget.com project. Not just subdomain, but it gives you information about DNS server, MX record, TXT record, and excellent mapping of your domain.
NMMAPPER
An online tool to find subdomains using Anubis, Amass, DNScan, Sublist3r, Lepus, Censys, etc. I tried NMMAPPER for one of the domains, and the results were accurate. Go ahead and give it a try for your research works.
Sublist3r
Sublist3r is a python tool to find subdomains using a search engine. Currently, it supports Google, Yahoo, Bing, Baidu, Ask, Netcraft, Virustotal, ThreatCrowd, DNSdumpster, and PassiveDNS. Sublist3r is supported only on Python 2.7 version and has few dependencies in a library. You can use this tool on Windows, CentOS, Rehat, Ubuntu, Debian, or any other UNIX-based OS. The following example is from CentOS/Linux.
Login to your Linux server Download latest Sublist3r
Extract the downloaded file
It will create a new folder called “Sublist3r-master”
As I mentioned earlier, it has the following dependencies, and you can install it using a yum command. Now you are set to discover the subdomain by using the following command. As you can see, it did discover my subdomains.
Netcraft
Netcraft has a large number of domain databases, and you don’t want to miss this in finding public subdomain information. The search result will contain all the domains and subdomains with first seen, netblock, and OS information. If you need more information about the website, click on-site report, and you will be given tons of information about technologies, ranking, etc.
Detectify
Detectify can scan subdomains against hundreds of pre-defined words, but you can’t do this to a domain you don’t own. However, if you have authorized a user, you can enable subdomain discovery in the overview under settings.
SubBrute
SubBrute is one of the most popular and accurate subdomain enumeration tools. It’s a community-driven project, and it uses the open resolver as a proxy, so SubBrute doesn’t send traffic to the domain’s name servers. It’s not an online tool, and you need to install this on your computer. You can use Windows or UNIX-based OS, and installation is very easy. The following demonstration is based on CentOS/Linux.
Log in to your CentOS/Linux Download the latest SubBrute
Unzip the downloaded zip file
It will create a new folder called “subbrute-master”. Go inside the folder and execute the subbrute.py with the domain. It will take a few seconds and result in you with any subdomain found.
Knock
Knock is another python-based subdomain discovery tool tested with Python 2.7.6 version. It finds the subdomain of a target domain using a wordlist.
You can download and install this on a Linux-based OS.
Extract the downloaded zip file with unzip command
it will extract and create a new folder, “knock-knock3.“ Go inside this folder and install with the following command
Once installed, you can scan for subdomains by following
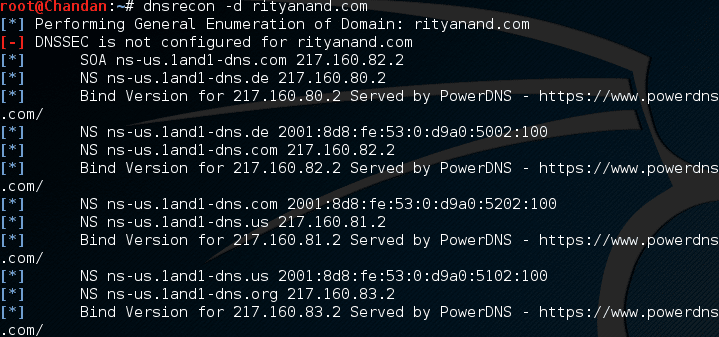
DNSRecon on Kali Linux
Kali Linux is an excellent platform for a security researcher, and you can use DNSRecon on Kali without installing anything. It checks all NS records for zone transfers, overall DNS records, wildcard resolution, PTR record, etc. To use DNSRecon, execute the following, and you are all done.
Pentest-Tools
Pentest-tools search for subdomain using multiple methods like DNS zone transfer, DNS enumeration based on wordlist, and public search engine. You can save the output in PDF format.
MassDNS
If you want to resolve domain names in bulk, MassDNS is the tool for you. This tool can resolve over 350,000 domain names per second! It uses publicly available resolvers, and it is suited for people who want to resolve millions or even billions of domain names. One issue you may face while using this tool is that it may increase the load on public resolvers and lead to your IP address being flagged for abuse. Therefore, this tool must be used with caution.
OWASP Amass
Amass has been created to help information security professionals perform network mapping of attack surfaces and perform external asset discovery. The tool is entirely free to use, and its clientele includes the leading IT company Accenture.
Conclusion
By using the above tools, I hope you should be able to discover subdomains of the target domain for your security research. You may also want to try an online port scanner. If you are interested in learning ethical hacking, check out this course.